Our research on multi-factor authentication (MFA) solutions highlights various adaptive authentication methods (e.g., offline authentication) offered by leading software providers. To highlight how companies like Apple, PayPal, and Google use these methods, we provided 10+ real-life MFA examples of authentication types and methods:
- Examples of MFA types:
- Examples of MFA methods:
Read more: Multi-factor authentication (MFA) pricing and plans, MFA use cases.
Identification through what the user knows
Using information only the user knows (e.g., passwords, PINs, and security questions) as an authentication step is best suited for low-level security applications (e.g., basic website accounts) due to vulnerabilities. Thus, identification-based can be easily compromised. For example, passwords and security answers can be stolen through phishing attacks.
Some common examples of this type of authentication include:
- Passwords: Users enter a pre-selected string of characters (letters, numbers, and symbols) to gain access. This is the most widely used authentication factor.
- Security questions: Users answer personalized questions (e.g., “What is your mother’s maiden name?”) as a secondary identity verification method.
- Personal identification numbers (PINs): A numeric code (usually 4-6 digits) chosen by the user, often used for ATM transactions, mobile banking, or device unlocking.
Identification using something the user possesses
This approach uses a physical asset or information explicitly supplied to the user. This next-level identification method is useful for confirming identification, as long as users avoid phishing attacks by hackers who can steal the information.
In situations where users are vulnerable to phishing attacks hackers may attempt to steal security codes, organizations should implement:
- Multi-layered authentication, combining possession-based factors (e.g., SMS verification codes) with biometric authentication (Face ID, fingerprint scans)
- or identification through location and time that detects unusual behavior.
Here are some examples of an identifier a user can possess:
SMS verification codes
SMS verification codes require users to enter a password and confirm their identity by entering a one-time passcode (OTP) sent to their mobile phone via SMS. This authentication type can be a secondary method for less critical applications.
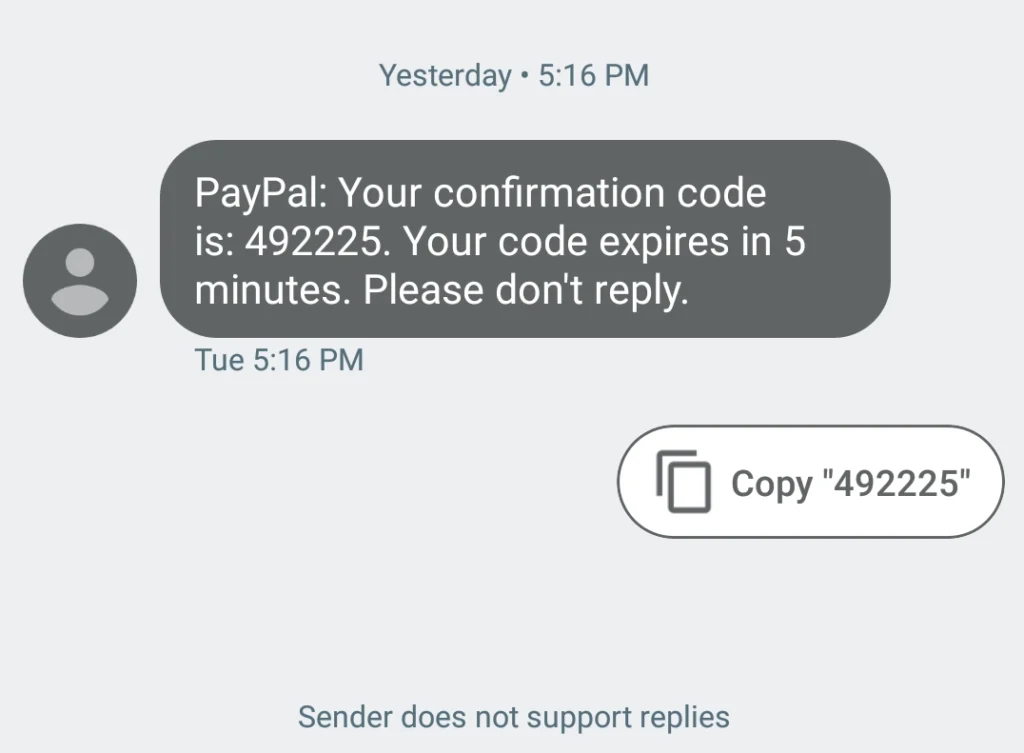
Real-life example:
PayPal offers SMS-based authentication as an additional verification layer. PayPal sends a one-time password (OTP) via SMS, when a user logs in from an unrecognized device or location, requiring the user to enter the code to complete authentication..

Mobile app push notifications
Mobile app push notifications are real-time authentication methods where users receive a push notification on their registered mobile device asking them to approve or deny a login attempt.
This provides an efficient alternative to SMS-based OTPs, reducing the risk of phishing and SIM-swapping attacks.
Real-life example:
ManageEngine ADSelfService Plus, an identity security solution with MFA alerts Active Directory users about their password status and self-service operations via push notifications to their mobile app.
Source: ManageEngine
YubiKey hardware tokens
The point of Yubikeys is to have a hackproof physical key in your pocket to protect your account. It is ideal for high-security environments such as financial institutions and government agencies.
Yubikeys generate OTPs or use FIDO2 authentication to grant secure access to applications and systems. FIDO2 authentication is an open authentication standard that utilizes public key cryptography to enable strong passwordless authentication. It helps MFA solutions resist phishing, and man-in-the-middle (MITM) attacks.
Real-life example:
Hyatt Hotels uses YubiKey to enhance security across its global operations. Partnering with Microsoft, Hyatt Hotels replaced its mobile-based MFA with phishing-resistant MFA using YubiKeys.This transition improved security for applications handling personally identifiable information (PII) and cardholder data.
Smart cards
Smart cards are credit card-sized gadgets with a microprocessor and a secure storage place for sensitive data. Users need to physically insert their smart card into a card reader to verify their identification.
Real-life example:
The U.S. Department of Defense (DoD) uses a common access card (CAC). The DoD issues CACs to military personnel, civilian employees, and contractors. These smart cards serve as standard identification for access to DoD computers, networks, and certain facilities, ensuring secure and authenticated entry.
Identification through who the user is
The identification type relies on something you are, using biometric data to verify identity. It leverages unique biological traits that are difficult to replicate, making it more secure than traditional password-based authentication and identification types using something the user possesses.
Biometric authentication (Fingerprint, Face ID, Optic ID)
Biometric authentication uses unique physical characteristics like fingerprints or facial recognition to verify a user’s identity. Biometric authentication is more secure when combined with another MFA method, such as a password.
Real-life examples: Apple’s Face ID & Touch ID & Optic ID:
- Touch ID (2013): Uses fingerprint recognition for unlocking devices, Apple Pay, app authentication, and more.
- Face ID (2017: Uses facial recognition with a camera for secure device access and authentication.
- Optic ID (2024): Uses iris recognition on Apple Vision Pro for secure access and payments.
Source: Apple
Identification through location and time
This component, also known as adaptive authentication, is the latest and most complex type of authentication. It includes location, time, and behavior. This method uses AI, GPS, and contextual data to generate a risk rating and assess whether a login attempt is legitimate or requires additional verification.
Geolocation-based authentication
Geolocation authentication enables users in a certain geographic region to access your resources without the need for credentials such as a library barcode number or a login and password. Businesses that allow access to all users inside a certain state, region, nation, or comparable geographic area use geolocation authentication.
How it works:
- IP address & geo-fencing: The system checks the user’s IP address and geolocation to determine their location. If the login request comes from a recognized (whitelisted) location, access is granted.
- GPS & Wi-Fi triangulation: Mobile applications can verify a user’s location using GPS data or Wi-Fi networks to confirm legitimacy.
Real-life example:
Okta’s MFA tool enables location-based authentication. With Okta MFA, organizations can enforce location-based access control, restricting or granting access to a tenant based on geographic location. This feature allows admins to define dynamic zones within the Okta admin panel, ensuring that only traffic from approved regions—such as the United States—is allowed. You can define a dynamic zone on the Okta admin page:
Source: Okta
Time-based one-time passwords (TOTP)
TOTP authentication generates temporary codes using an algorithm and a shared secret key, requiring users to enter the code within a specific time frame. TOTP authentication is used for medium to high-security applications.
Real-life example:
Google & Authenticator Apps Google enforces TOTP via its Google Authenticator app. Many services like Dropbox and Amazon AWS also implement TOTP-based MFA.
Offline authentication for remote and network access
MFA is not possible when an authentication server is unavailable or inaccessible. In such cases, offline multi-factor authentication is critical for improving endpoint and network security.
A common offline MFA solution uses hardware tokens or smart cards that generate unique one-time passcodes (OTP)), allowing users to authenticate without requiring an internet connection.
Real-life example:
RSA SecurID, an MFA solution, uses a hardware token for offline MFA. The RSA SecurID Token is a widely used offline multi-factor authentication (MFA) solution. It uses a hardware token to generate a time-based, one-time passcode (OTP) that is valid for a short period (typically 60 seconds). The generated OTP is used with the user’s username and password to complete the authentication process.
Role-based authentication for granular access control
Role-based authentication (RBA) is a security mechanism where access to resources is granted based on user roles within an organization.
MFA can be used alongside RBA to enhance security by requiring multiple authentication factors based on the user’s role. This ensures that individuals only have access to the information and systems necessary for their job, providing an added layer of security.
Real-life example:
Interfaith Medical Center’s IT administrators used ManageEngine ADManager Plus, an identity governance and administration (IGA) solution, to allow MFA for large-scale access control tasks. With ADManager Plus, the company could create, delete, and modify multiple Active Directory (AD) accounts in a single operation.
Interfaith Medical Center stated that after implementing bulk role-based access control, they were able to manage 1000+ user objects, 750+ mailboxes, and 850+ workstations with two admins and five help desk specialists.
Risk-based authentication
Risk-based authentication assesses the probability of account compromise with each login.
Risk-Based Authentication (RBA) is an adaptive security approach that evaluates the risk associated with each login attempt by analyzing various contextual factors. Based on the assessed risk level, the RBA tool dynamically adjusts the authentication requirements.
If a login request appears unusual or suspicious, the system triggers RBA, requiring the user to provide additional verification factors (e.g., fingerprint, Face ID).
Key parameters considered in RBA:
- Time of access: Unusual login times compared to the user’s typical behavior.
- Geolocation: Login attempts from unexpected or new locations.
- Device and browser information: Use of unfamiliar devices or browsers.
- IP address: Access from IP addresses with suspicious activity or from different regions.
- User behavior: Deviations from historical usage patterns.
Real-life example:
Mastercard uses RBA in its systems to analyze multiple risk signals in real time. It detects unusual locations, new devices, and high-value purchases that deviate from a cardholder’s normal behavior. If flagged as high risk, the system triggers additional authentication via Mastercard Identity Check (3D Secure 2.0) to prevent fraud.
Machine-based authentication
Machine-based MFA is an authentication approach that relies on trusted devices and hardware-level security as an additional factor in verifying a user’s identity.
Unlike traditional MFA, which often uses passwords, machine-based MFA integrates authentication directly with:
- registered devices
- encryption protocols
For example, when a user registers a device, the MFA system generates a unique cryptographic key pair (public and private keys), a method of encrypting data. The private key stays on the user’s device, while the public key is stored on the service’s servers.
Real-life example:
Google uses passkey support, allowing users to authenticate using cryptographic keys stored on their devices. This method replaces traditional passwords with device-based authentication.